Hey there! I’m Jeremiah Byerley, a technical consultant, author, and former CTO of Lynda.com (but don’t worry, I’m not here to bore you with corporate stories). I’ve had the privilege of working with companies like Higher Octave Music, EMI, Activision, IDIMedia, and Storyful, and now I’m here to share my tech knowledge with you.
On my website, you’ll find a bunch of tutorials and articles covering all sorts of tech topics. From step-by-step fixes, artificial intelligence to cloud computing and cybersecurity, I’ve got your back (just don’t ask me to fix your printer, I can’t work miracles).

Gotop (gotop) is my new favorite linux command. I have it running on all my servers & Macbook,…

The use of propriety SSD’s on MacBooks limits the amount of space to dual boot Windows and MacOS on the…

The use of propriety SSD’s on MacBooks limits the amount of space to dual boot Windows and MacOS on the…

All from Trader Joes: One jar Tomato basil marinaraOne bag quarto formaggioBox of oven baked Lasagna noodlesBroccoli (the devil’s vegetable…
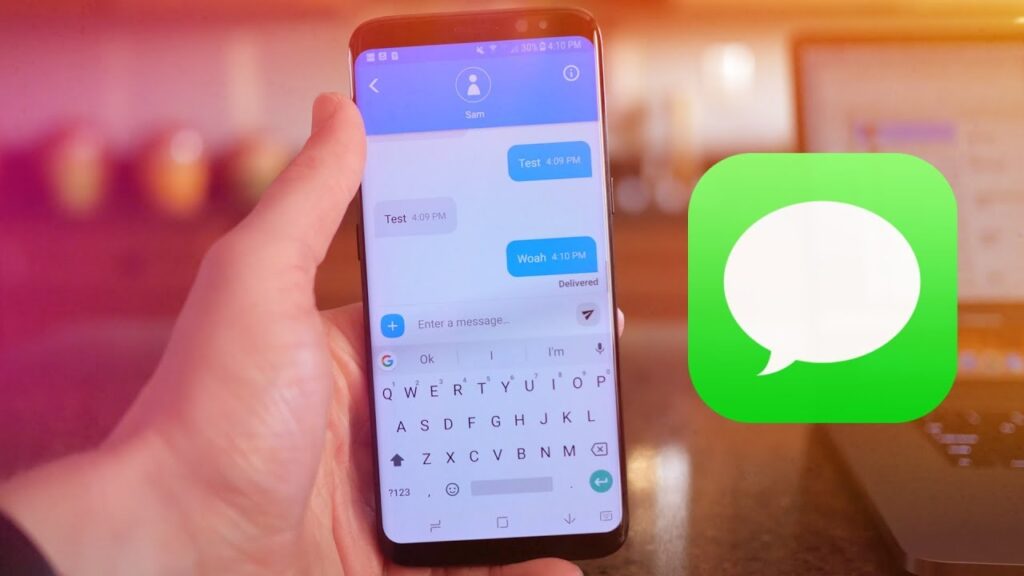
One of the major differences with an iPhone and Android is iMessage. iMessage is Apples propitiatory messaging systems that blends…

Many small computers and laptops have an M.2 slot for adding an SSD to a computer but did you know…

As we use different passwords in different browsers, it can be hard to track down which browser has the stored…

A lot of us are tied to Google's and Apple's calendaring systems. Having both, it can be tough to keep…

I've had a Logitech Bluetooth keyboard for a few years, it got stuck paired to a device and it basically…
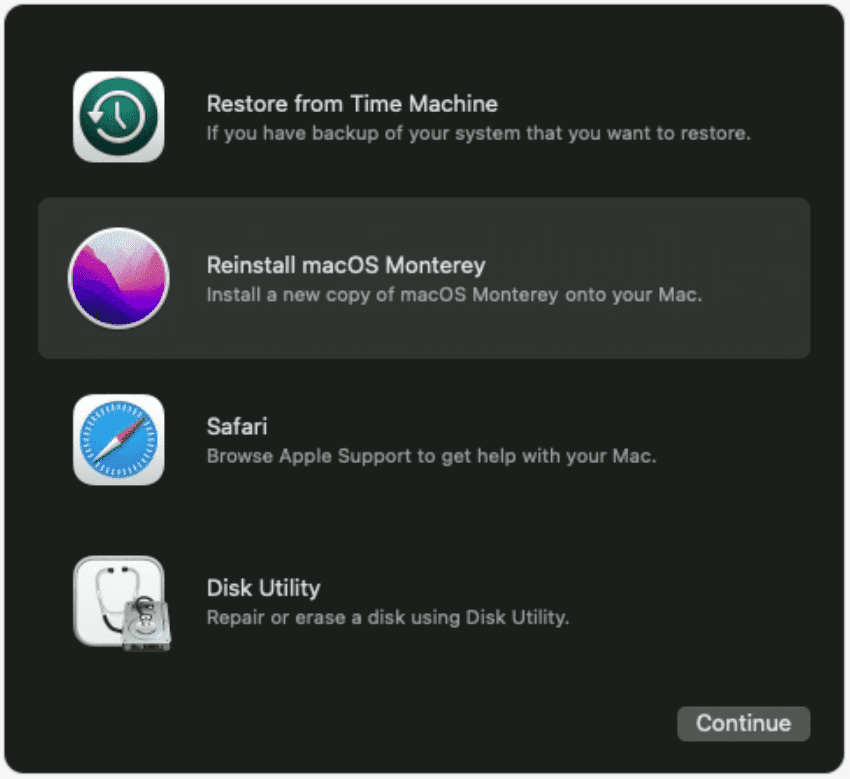
Booting into recovery mode on a Mac usually requires rebooting the computer and holding option + R. There are times…